Exploring the World of Cryptographic Protocols
Cryptographic protocols form a basis of securely running operations in the current society in light of the increased adoption of digital services. They support the secrecy, accuracy, and validity of data communication within and across borders of globe. According to the growth of using computerized structures, the knowledge of such protocols is important not only to the users but to those who are creating them.

In this tutorial, we shall discuss more about cryptographic protocols embracing the necessity of the cryptographic protocols, the main categories of the cryptographic protocols, the methods of constructing and implementing the cryptographic protocols, real-world usages of the cryptographic protocols and prospects for their development.
Understanding Cryptography
In other words, cryptography is the process of disguising the information in such a way that it cannot be understood by any unauthorized persons while those who are authorized to understand it can easily decode it using a code which has been given to them and which is referred to as the decryption key. Hiding of messages is as old as the world itself with world leaders and commanders being in great need to ensure privacy of their messages. However, under the advanced development of technology and digital cracking cryptographic mechanism turned into a completely developed scientific discipline.
Purpose of Cryptography
Cryptography is required for the following main reasons:
- Confidentiality: Limit the disclosure of information to only those who were supposed to; this aspect is vital inside an organization.
- Integrity: Ensuring that the given information is not changed accidentally or deliberately.
- Authentication: This is the process of confirming the identities of the parties of communication.
- Non-repudiation: Non-repudiation means that it is impossible to get the services of a certain party to deny the receipt of a message, or the signing of a certain document.
Cryptographic Protocols: An Overview
Cryptography is divided into two parts which are the cryptographic units and protocols, whereby cryptographic protocols refer to the sequences of the cryptographic operations. That is how the algorithms and keys must be applied to meet the desired security objectives. These protocols are vital in developing layers of security for the data while in transit within the internet, an organization’s intranet, mobile service provider networks, etc.
Key Components of Cryptographic Protocols
Cryptographic protocols refer to complex techniques that may involve the use of cryptographic mechanisms aiming at providing certain security requirements. These are the main items that comprise these protocols:
- Algorithms: These are a set of mathematical or computational formulas that are used in conducting encryption and decryption. Some of the more commonly used symmetric key algorithms such as the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES) while the others are the asymmetric key algorithms such as the Rivest-Shamir-Adleman (RSA) algorithm and the Elliptic Curve Cryptography (ECC).
- Keys: These are numerical values that are used for performing the encryption and decryption operations on the data. In symmetric key algorithms, both the encrypting and decrypting processes involve the usage of the same key while in the asymmetric key algorithms there are two keys: the public key and the private key.
- Hash Functions: This is a certain algorithm that performs mapping that takes an input, or ‘message’ and produces a fixed-size string of bytes. The hash functions are part of data integrity and are employed in digital signatures as well as in message authentication codes (MAC).
- Digital signatures: These are important when it comes to proving the source as well as the contents of a given message. A digital signature is produced with the help of the sender’s private key and can be decrypted by the recipient having the sender’s public key.
- Protocols: A structured sequence of operation that describes the way in which cryptographic technology is implemented to achieve stated security goals. Some of them are SSL/TLS for secure web connection, SSH to remotely login securely, PGP for secure mailing.
How Cryptographic Protocols Work
Cryptographic protocols follow certain procedures to implement security over communication between different parties. Here is an account of some of the procedures:
Key Exchange
To facilitate encrypted communication, there must be an agreement between the two participants on which key or which set of keys is to be used. This is practiced in symmetric key cryptography where commonly used key exchange is the Diffie Hell’s Key exchange where two users share a secret key over an insecure channel. Asymmetric cryptography makes this process easier in that the key that is normally known as the public key can be made public.
Authentication
It provides an assurance that the communication partners are genuine. Authentication can be done with certificate capabilities provided by the SSL/TLS protocols with the help of the trusted Certifying Authorities (CA). It needs to be noted here that public key infrastructure (PKI) is often employed for this purpose.
Encryption
After keys establishment and parties’ identification, the information is encrypted by using the adopted cryptographic algorithm together with the key. This makes it possible for even if the information being transmitted over the network to be intercepted, it cannot be comprehensible to the wrong hands.
Retransmission and Data Checks
Last, there is the aspect of hash functions and the message authentication code that works to check whether or not data has been altered in the course of transmission. These create a hash value or code of the data and the recipient can easily check if this code matches with the data sent to ensure that the latter has not been tampered with.
Decryption
After the data has been encrypted, it can be decrypted where the received information can be deciphered to the intended format by using an appropriate key.
Verification
Finally, the recipient verifies the data and ensures it is accurate and from the source it is claimed to have come from. For digital signatures, the actuality and validity of the signature is checked by the receiver with the help of the sender’s public key which ensures that the data has originated from the claimed sender and has not been tampered in any way.
Types of Cryptographic Protocols
Cryptographic protocols can be classified from their purpose and use in the system. Here it is useful to present the types that are most important and widely used in various Internet services:
Symmetric Key Protocols
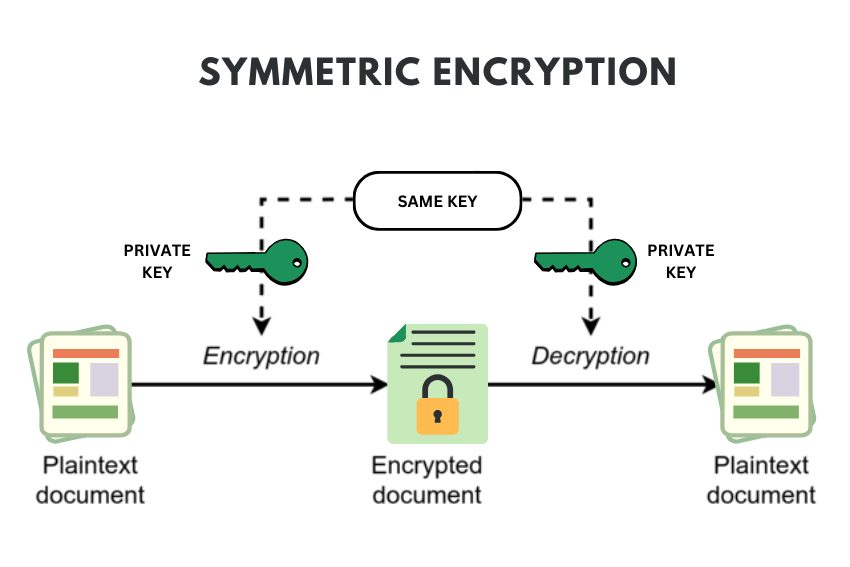
Sharing of central scheduler among parallel video decoders is viewed as efficient since it encourages the use of symmetric key protocols that involve the use of a single key for coding and decoding. These are faster than the asymmetric ones and are used where speed is a crucial factor and thus ideal for use in encryption of large amount of data.
Examples
- AES (Advanced Encryption Standard): Used for protecting data, it is actually the encryption technology chosen by the US administration.
- Triple DES/3DES: This is an improvement of the Data Encryption Standard (DES) where the DES cipher algorithm is applied thrice on every data block.
Applications
The cases of using symmetric key protocols are as follows:
- Data Encrypted: It refers to the protection of data that is stored on computer or in other media or in a database.
- Secure Communication: Some other protocols include the Internet Protocol security or IPsec and Transport Layer Security or TLS, some of which may involve the use of symmetric key for the encryption of the message body after key exchange.
Also Read – Symmetric vs Asymmetric Encryption: Key Differences Explained
Asymmetric Key Protocols
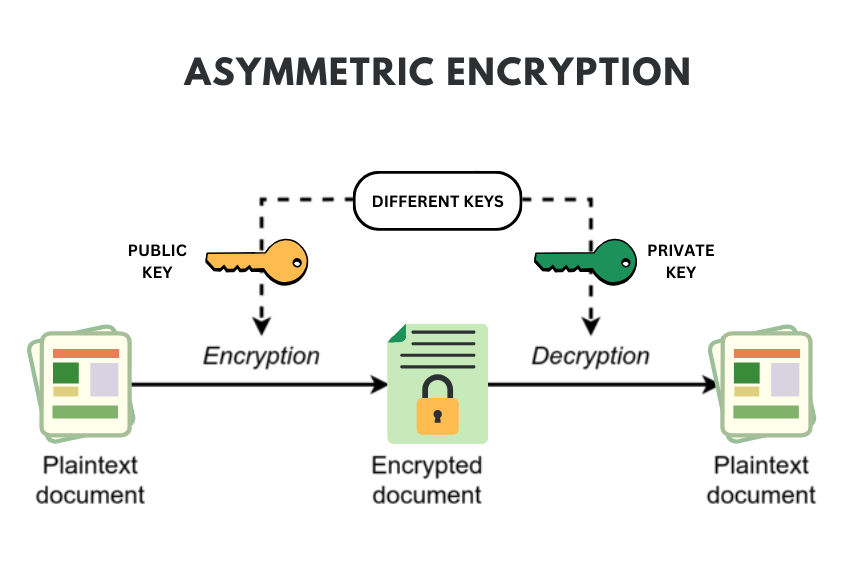
The asymmetric key protocols, known as the public key cryptography, involve two keys shown where the key for encryption is a public key and another one for decryption being a secret key. This key pair mechanism is used to easily overcome some of the weaknesses or issues with symmetric key cryptography for instance the issue with key distribution.
Examples
- RSA (Rivest-Shamir-Adleman): It is one of the earliest developed public key cryptography system, used mostly in secure data encryption.
- ECC (Elliptic Curve Cryptography): It has better security as it offers the same security as RSA but in smaller key than RSA.
Applications
The following are some of the key advantages that asymmetric key protocols play in:
- Secure Key Exchange: It is protocols such as the Diffie-Hellman and its elliptic curve version known as ECDH that enables secure exchange of keys over an insecure channel.
- Authentication: The message was sent as who it says it was, without anybody modifying it and DSA (Digital Signature Algorithm) or ECDSA (Elliptic Curve Digital Signature Algorithm) to validate that it was.
Also Read – AES vs RSA Encryption: Understand Key Differences
Hash-Based Protocols
Hash protocols use hash functions to prove the authenticity of the data they are dealing with through hashing. A hash function accepts an input and results in a string of fixed number of bytes normally referred to as hash value or the digest.
Examples
- SHA-256 (Secure Hash Algorithm 256-bit): Another hash function from the SHA-2 family dedicated to numerous security-related processes and procedures of the TCP/IP model, such as TLS and SSL.
- MD5 (Message Digest Algorithm 5): It is one of the famous Digest Algorithms though it is now outdated and can be considered cryptographically broken and cannot be used in further applications.
Applications
Hash-based protocols are used in:
- Data Integrity: This means verifying that data has not been tampered with during its transmission.
- Password Storage: Most will store a password as hashed words for the purpose of security.
Hybrid Protocols
Hybrid schemes are vicious that use at least symmetric and asymmetric cryptography to take advantage of each side. The principle of the operation is that asymmetric cryptography is used to exchange the keys while symmetric cryptography is employed in data encryption.
Examples
- TLS (Transport Layer Security): HTTP website traffic is secured through a TLS protocol which employs either RSA / ECC for exchanging the keys and AES for the purpose of data encryption.
- IPsec (Internet Protocol Security): A protocol used for the protection of IP connection protocols, which involves confirming and encrypting an IP packet on a connection.
Applications
Hybrid protocols are prevalent in:
- Internet Browsing: TLS plays dual roles in relating to HTTPS; safe web browsing and safe handling of internet applications.
- Virtual Private Networks (VPN): IPsec is used in providing security to the internet connection in VPNs.
Quantum-Resistant Protocols
Quantum computing has brought the threat to traditional cryptography because existing algorithms on the market can be easily solved by quantum algorithms. Quantum-resistant protocols are particularly designed to be immune to quantum attacks.
Examples
- Lattice-based Cryptography: It cannot be easily attacked by the quantum computer thus considered to be a strong candidate for post quantum cryptography.
- Hash based: Some hash-based signatures are also said to be post quantum secure.
Applications
Quantum-resistant protocols are crucial for:
- Simplifying Security: Long term resilience in a post-quantum environment.
- Government and Military Communication: Where long-term confidentiality is the measure of time.
Real-World Applications of Cryptographic Protocols
There are many applications that need a secure way to share information with other parties and cryptographic protocols play a key role in all those applications.
- Secure Web Browsing: TLS is at the foundation of safe browsing in the World Wide Web since it confirms that data between the browser of a user and a web server is secure.
- Secure Email: Some of the methods that are applied for protecting e-mail communications include S/MIME (Secure/Multipurpose Internet Mail Extensions) and PGP (Pretty Good Privacy).
- Secure File Transfer: The two protocols that ensure security in file transfer are FTPS (File Transfer Protocol Secure and SFTP (SSH File Transfer Protocol) since the data is encrypted.
- Virtual Private Networks (VPNs): VPNs employ different standards such as IPsec and SSL/ TLS for establishing secure connection over the internet in order to provide remote connectivity to a private network.
- Secure Messaging: Examples of such applications include WhatsApp and Signal, and use of cryptography to secure end to end communications so as to eliminate intercepting of messages.
Challenges and Future Trends
Nonetheless, cryptographic protocols are far from perfect and are plagued with some challenges and need improvement due to various factors.
- Quantum Computing: Quantum computers threaten to endanger many of the current cryptographic protocols, especially those that rely on the use of asymmetric cryptography. This problem is being tackled by quantum-resistant algorithms.
- Implementation Flaws: Since protection is merely a protocol, even the tightest security measures can be penetrated because of negligence. Security measures have to be taken into account and it is important to conduct the audit of the code.
- Scalability and Performance: With the amount of data being used and the number of users growing, cryptographic cannot compromise on security while at the same time aiming to optimize its throughput.
- Blockchain and Cryptocurrencies: Cryptographic protocols are central to the accomplishment of blockchain technology and it’s based on digital currencies. It is still an active line of investigation finding more enhanced and secure protocols.
Conclusion
Protocol is at the very heart of the world relying on digital means of protection as the means of securing data. Some common uses of the cryptographic hash functions to include securing web communications to use of the technology for ensuring that online transactions that involve the use of cryptocurrencies are secure.
Cryptographic protocols are one of the main weapons to protect against attacks on information and can be adapted to emerging threats to bolster the protection of systems. These protocols are quite useful for anyone to familiarize with when that is involved in the design of secure systems, implementation, or management.
New technology will continue to appear but cryptographic protocols will follow it as a result of which data and information will continue to be safeguarded.