Introduction to AES vs RSA
Explore the key differences between AES vs RSA encryption. Understand their pros, cons, and uses to secure data effectively.
Encryption is that technique through which messages or data or information are made so secured or coded that only the intended recipient can read or understand it. Encryption and decryption use complex mathematics and a key to put data into the form that cannot be read and convert it back. At present, the most popular forms of cryptography are AES encryption and RSA encryption. Therefore, the likelihood remains as to what the differences between AES vs RSA encryption processes are. In this article, the basics of AES and RSA encryption will be described and some points of difference will be marked.
What is AES Encryption?
Current AES is a type of symmetric-key cipher that was developed and selected by the US National Institute of Standards and Technology (NIST), being the material part of an encryption standard that was solidified and implemented after five years of standardization. It is derived from the Rijndael cipher which was developed by two Belgian cryptographers Joan Daemen and Vincent Rijmen. AES is used globally today to protect data and messages in electronic devices.
How AES Works
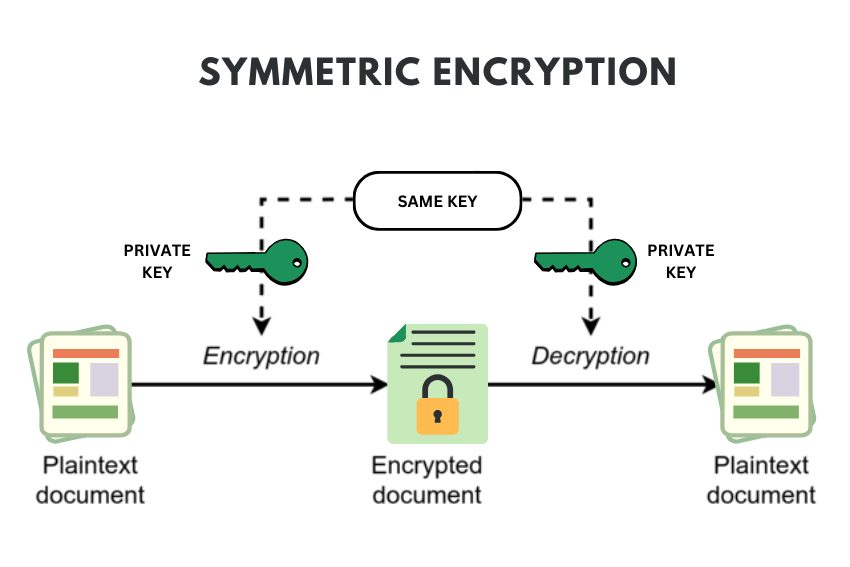
In AES, a secret key is also employed which transforms the plaintext (the original unencrypted data) and inputs it into cipher algorithm to encrypt the data. It has to be known to the sender and the recipient as to encrypt and decrypt the message from the other. Being an example of a symmetric key algorithm, the same key is used for the encryption and decryption of the message. The AES keys may have key sizes that are 128/192/256 bits. Today there are two basic key sizes: 128 and 256 bit.
The AES encryption algorithm uses byte data in the form of a 4×4 matrix which is implemented by column and called the State array. It consists of 4 basic transformations that are used repetitively in multiple encryption rounds:
- SubBytes – a non-linear byte substitution
- In the present case, there is ShiftRows – it is a transposition step that takes hours 4-10.
- MixColumns – A Linear Mixing Operation
- AddRoundKey – subtract a round key from a byte.
The number of rounds is also decided by the key size,
- 10 rounds for 128-bit keys
- 12 rounds for 192-bit keys
- 14 rounds for 256-bit keys
Every round employs a unique 128-bit round key derived from the original encryption key with the help of a key schedule.
Decryption utilizes a similar cipher algorithm but in reverse by applying the inverse of transformations and the round keys in an inverted manner. AES being symmetric in nature, the enciphering key used is same as deciphering key used in the procedure.
Advantages of AES
- Speed: AES can basically encrypt data at a very fast rate and it is ideal for emplacing cipher key on large chunks of data. This makes it suitable for loading applications that require excellent high-performance encryption including video streaming service and disk encryption.
- Security: AES is as secure as it can be, and no one has been able to develop any type of attack that could compromise it when used appropriately. The possibilities of the key length (128, 192 and 256) allow for choices of various levels of security required.
- Wide Adoption: AES is obtained for use in many types of industries for government, military and financial businesses, thus it is a standard encryption.
Disadvantages of AES
- Key Management: However, an actual issue of symmetric encryption is the need for a secure method of managing keys. Once the key is exposed, the data becomes exposed to anyone as the information is decrypted without any problem.
- Lack of Authentication: AES has no authentication controls integrated meaning that although it protects the data, it does not confirm the absolutes of the message.
What is RSA Encryption?
RSA encryption is by far the most famous public-key encryption technique that can be found in the world today. It was patented by Ron Rivest, Adi Shamir, and Leonard Adleman in 1977 although they first publicly described it in 1978. The RSA algorithm obtains its security from the problem of factoring big primes as it becomes almost impossible to do it.
How RSA Works
Different from other key algorithms such as the advanced encryption standard AES that uses the same secret key for both encryption and decryption, RSA is an asymmetric key in that it employs a public key and a private key.
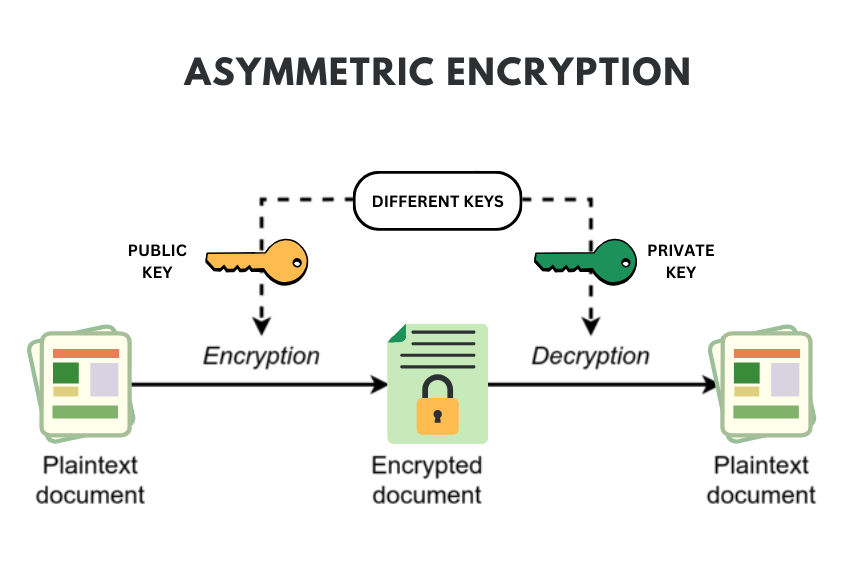
The public key is distributed to whoever wants to communicate secrets through it, it is shared to anyone. The other is a private key and it is only revealed to the intended recipient so that they spotted between these two is encrypting and decrypting function.
The algorithm is used to encrypt any message using the recipient’s public key while the recipient uses the former to decrypt the said message using a private key. This attribute enables RSA to be used for authenticating the identity of the sender, and this guaranties secure transfer of data.
The RSA algorithm involves three steps:
- Key Generation: The private key and the public key are usually derived from two very large prime numbers and controlled by means of complicated calculations. These two keys are such that the public key is given to any member in the network or anybody while the owner only knows the private key.
- Encryption: Here the sender encodes the message using the recipient’s public key.
- Decrypting: The message is decrypted by the recipient using a private key.
The security of RSA encryption does not lie with the concealment of the ciphering scheme but rather in the almost infeasibility of factorizing very large primes. To illustrate, deciphering this product even if the encryption key is known is nearly historically impossible if the primes are unknown to the decipherer. This makes it possible to share encryption keys in the open without any form of insecurity.
Advantages of RSA
- Secure Key Exchange: RSA makes communication secure key exchange is established without prior exchange of any secret key. This makes it suitable for creating secure connections over the world wide web, like the SSL/TLS.
- Digital Signatures: RSA can be used for digital signatures – in other words, the messages’ sender and the integrity of a message can be authenticated and confirmed.
- Widely Respected: RSA is one of the original examples of the public-key cryptosystems and today it is widely recognized and popular among other security professionals.
Disadvantages of RSA
- Speed: RSA is significantly slower than symmetric encryption algorithms like AES, particularly when encrypting large amounts of data. That is why it is usually used in conjunction with other symmetric algorithms in which RSA is used to encrypt a symmetric key, while the latter generates data encryption.
- Key Size: However, it should be pointed out that the level of security that can be achieved by RSA is achieved with the aid of larger key sizes than is the case with the symmetric keys. The latest practice has shown that a key of at least 2048 bits may be justified, and it creates additional computational load.
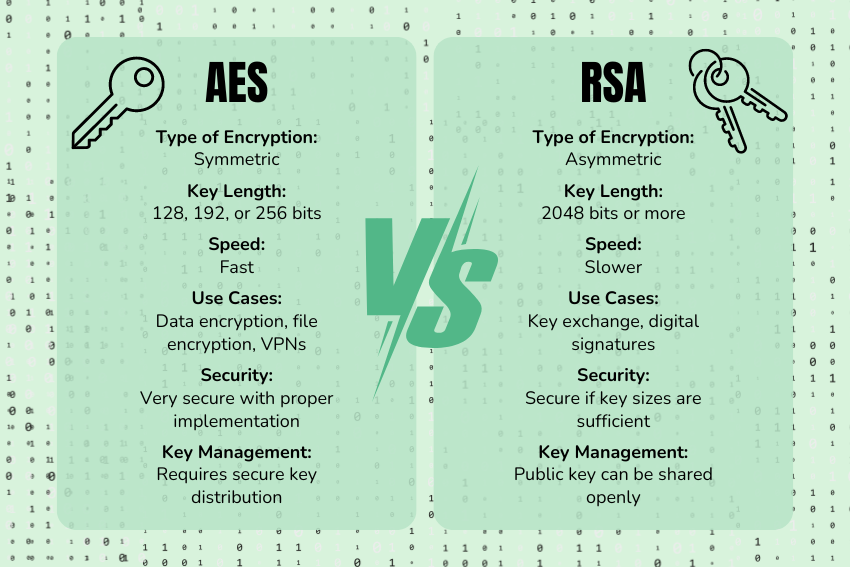
AES vs RSA Encryption: Quick Comparision
| Feature | AES | RSA |
|---|---|---|
| Type of Encryption | Symmetric | Asymmetric |
| Key Length | 128, 192, or 256 bits | Typically, 2048 bits or more |
| Speed | Fast | Slower |
| Use Cases | Data encryption, file encryption, VPNs | Key exchange, digital signatures |
| Security | Very secure with proper implementation | Secure if key sizes are sufficient |
| Key Management | Requires secure key distribution | Public key can be shared openly |
AES vs RSA Encryption: Key Differences
While both are proven encryption algorithms that are widely used, there are some fundamental differences between AES and RSA encryption:
- AES is a type of block cipher algorithm which uses the symmetric key system while RSA is an algorithm of the asymmetric key system.
- AES is mainly employed for the processing of encrypting electronic data and files. RSA is used for securely transferring symmetric keys (like AES), key exchanges, authentications, signatures and DMS (digital right management).
- AES is considerably faster than RSA for volume data encryption. RSA is slower and cannot be used directly for data encryption.
- AES is another well-known symmetric block cipher; one of the security parameters concerning the key size is of particular interest on the subject. To RSA, key generation parameters are crucial more than key size In RSA cryptography.
- AES uses block size of 128 bits but has key sizes of 128, 192 or 256 bits. RSA key size depends on the modulus length. The most common lengths can be 1024, 2048, 4096, or even more.
- Safety of AES is determined by key length and safety of RSA is determined by the degree of difficulty of factoring very large numbers.
- While AES has a double employment as a method of encryption of data in transit and data deliberately left in the memory, the RSA method is used primarily for encrypting data being in transit.
- Essentially AES employs substitution and permutation at the byte level in the rounds of encryption or decryption. RSA depends only on the exponential and modulo multiplicative procedures where two values – very big numbers – are located.
AES vs RSA Encryption: Use Cases
When to Use AES
- Data at Rest: AES is ideal for encrypting files, databases, and storage systems where data must remain secure when not in use.
- Data in Transit: For applications requiring fast encryption and decryption of data being transmitted over networks, such as VPNs or secure web traffic, AES is the preferred choice.
- Performance-Sensitive Applications: Streaming services, cloud storage, and other performance-sensitive applications benefit from AES’s speed and efficiency.
When to Use RSA
- Secure Key Exchange: RSA is commonly used in scenarios where secure key exchange is necessary, such as establishing secure connections via SSL/TLS.
- Digital Signatures: For applications requiring authentication and integrity verification, RSA’s capability to provide digital signatures is invaluable.
- Small Data Encryption: RSA can be used to encrypt small amounts of data, such as session keys, which can then be used for symmetric encryption.
In conclusion
AES and RSA are two widely used encryption standards with quite dissimilar methods of operation and are generally implemented simultaneously. AES is inclined for safe massaging of large data elements and RSA is willing to secure the keys and the data through the public key encryption algorithm. The combination of AES for data and file encryption and RSA for key exchanges gives a good encryption solution.