Introduction to Symmetric vs. Asymmetric Encryption
Encryption is the process of transforming a presentation plan or certain data in a manner that makes it hard for other people to access. There are two main types of encryption: symmetric and asymmetric encryption. To master the basics of IT, cybersecurity or data management, anyone must learn the differences between symmetric vs asymmetric encryption. This article explores the definitions of symmetric and asymmetric encryption, how it works, pros and cons, how they differ and usage of each one.
Symmetric Encryption
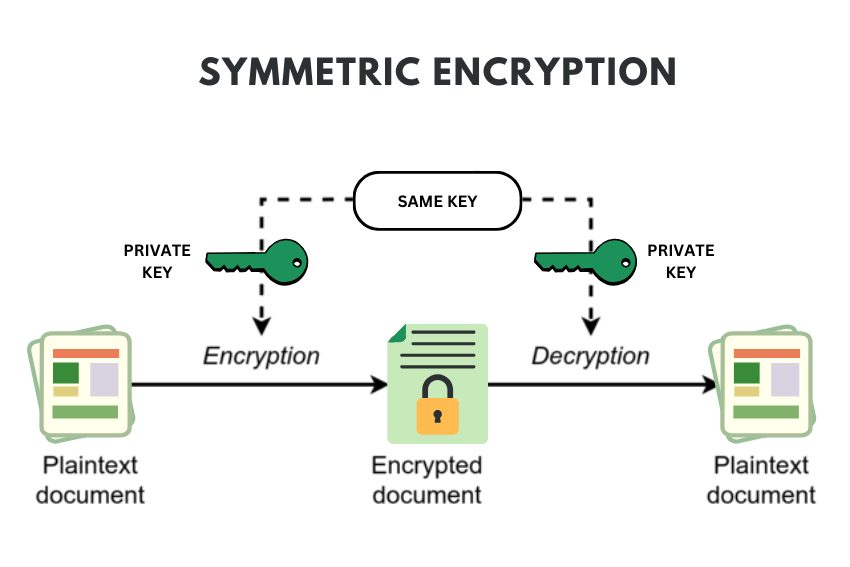
Enciphering and deciphering are exactly same in Case of symmetric encryption or also referred to as private key cryptography. This must be transmitted from one party to the other since this party will be using an encryption key to encrypt its messages and to decrypt messages from the other party. Here follows the list of symmetric encryption algorithms common today: AES, Blowfish, RC4, DES, and 3DES.
Key Properties of Symmetric Encryption
- Uses a single, shared key: The sender utilizes a key in an encrypted session and transmits the ciphertext to the receiver. The receiver also uses the same key to decipher the ciphertext and get the plaintext. Encryption and decryption use the same key without the need to exchange keys after an initial exchange like public key system.
- Faster processing: It must be noted that symmetric algorithms are much faster than asymmetric encryption and require simpler mathematical operations. This makes them well suited for encrypting large amounts of data that can be like files or even databases.
- Secure against brute force attacks: Secrets involved in symmetric encryption are often long and thus can hardly be guessed by an unauthorized user. As compared to the symmetric ciphers, asymmetric ciphers are less secure even if they are coded in the same number of keys.
- Vulnerable key exchange: The main weakness of symmetric encryption is the relative problem of exchanging a secret key between two communicating parties. Holders must make certain that they receive the right key during exchange; otherwise, security is at high risk. PKI can be commonly employed for secure delivery of the symmetric key.
How it Works
The process of symmetric encryption involves several steps:
- Key Generation: A secret key is generated, which is typically a random string of characters.
- Encryption: The sender uses the secret key to convert plaintext (the original message) into ciphertext (the encrypted message) using an encryption algorithm, such as the Advanced Encryption Standard (AES) or Data Encryption Standard (DES).
- Transmission: The ciphertext is sent to the recipient over a communication channel.
- Decryption: Upon receiving the ciphertext, the recipient uses the same secret key to convert the ciphertext back into plaintext.
Pros of Symmetric Encryption
- Speed: Symmetric encryption algorithms are generally faster than their asymmetric counterparts because they require less computational power. This makes them suitable for encrypting large amounts of data quickly.
- Simplicity: The implementation of symmetric encryption is relatively straightforward. With only one key to manage, both the encryption and decryption processes are uncomplicated.
Cons of Symmetric Encryption
- Key Distribution Problem: One of the main difficulties of symmetric encryption is generating a method for transmitting the secret key. It has been working on the principle that if the key is intercepted in between the communication then the security of the communication is utterly jeopardized. Hence, both parties need to respect the basic requirement of safe key exchange mechanisms.
- Limited Security for Sensitive Data: In case the same key is used in different sessions or communication, the chances of infiltration by the third parties are realized. Like any other type of symmetric key, if the owner of the key is lost, then all the information encrypted by that particular key, is compromised.
There are several practical applications of symmetric encryption as follows: VPN tunnels, full disk encryption, file or folder encryption and link encryption. This is also necessary to know that both TLS and SSL also use what is called symmetric encryption in order to connect safely to the Internet.
Asymmetric Encryption
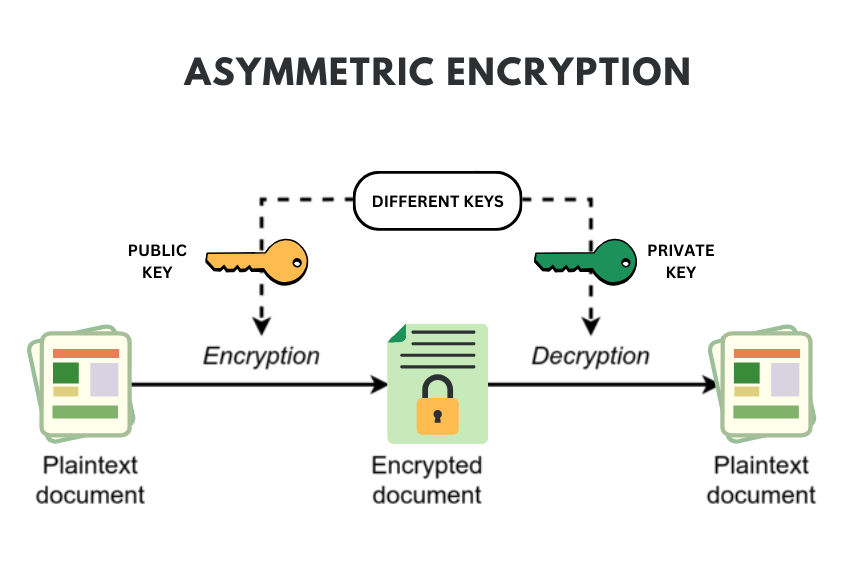
Public key encryption or asymmetric encryption utilize two keys which are the public key and the private key for encrypting and decrypting the data, respectively. The public key is made available while the private key is to be kept a secret all the time. For instance, some of the asymmetric algorithms are RSA, ECC, Diffie-Hellman, ElGamal and DSA.
Key Properties of Asymmetric Encryption
- Uses key pairs: Two mathematical related keys are used; one is the public key and the other is the private key. The public key is used to encipher the data while the only decipher can be done using the private key. And, similarly, information that one has encrypted with the help of the private key will be comprehensible only to the recipient who used the public key in the process. This is the basis of asymmetric encryption, which is a one-way mathematical relationship.
- Slower processing: Asymmetric ciphers use complicated mathematical transformations as opposed to XOR, substitution, etc. This makes their orders of magnitude slower than symmetric ciphers, particularly when large data has to be encrypted.
- Secure key distribution: The public key shall not be secured since for it to be used by different individuals to encrypt messages, it must be in the public domain. The only thing that needs to be protected is the private key itself by its owner. This does away with the major issue associated with key distribution in symmetric encryption.
- Used as building blocks: This method is not very useful for bulk encryption because it is slow in comparison to the other methods. However, it is employed to securely exchange the symmetric keys, messages for integrity through digital signing, and identity through certificates.
How it Works
The process of asymmetric encryption can be broken down as follows:
- Key Pair Generation: A key pair is generated, consisting of a public key and a private key. The public key can be freely distributed, while the private key is kept confidential.
- Encryption: The sender uses the recipient’s public key to encrypt the plaintext message into ciphertext.
- Transmission: The ciphertext is sent to the recipient over a communication channel.
- Decryption: Upon receipt of the ciphertext, the recipient uses their private key to decrypt the message back into plaintext.
Pros of Asymmetric Encryption
- Enhanced Security: Asymmetric encryption offers a higher level of security, especially for sensitive information. Since the private key is never shared, the risk of interception during key distribution is eliminated.
- No Key Exchange Needed: Since the public key can be shared openly, there is no need for secure key exchange methods. This simplifies the process of establishing secure communication.
Cons of Asymmetric Encryption
- Slower Processing Speed: Asymmetric encryption algorithms are generally slower than symmetric ones due to their complex mathematical operations. This can make them less suitable for encrypting large volumes of data.
- Complex Implementation: The use of key pairs can complicate the implementation of encryption systems, requiring more sophisticated management and storage solutions.
Some real-world use cases of public-key encryption include use of TLS/SSL to secure the Hypertext Transfer Protocol (HTTP), Pretty Good Privacy (PGP) for secure email, bitcoin, code signing where code authenticity is required as well as the use of digital signatures.
Symmetric vs Asymmetric Encryption: Key Differences
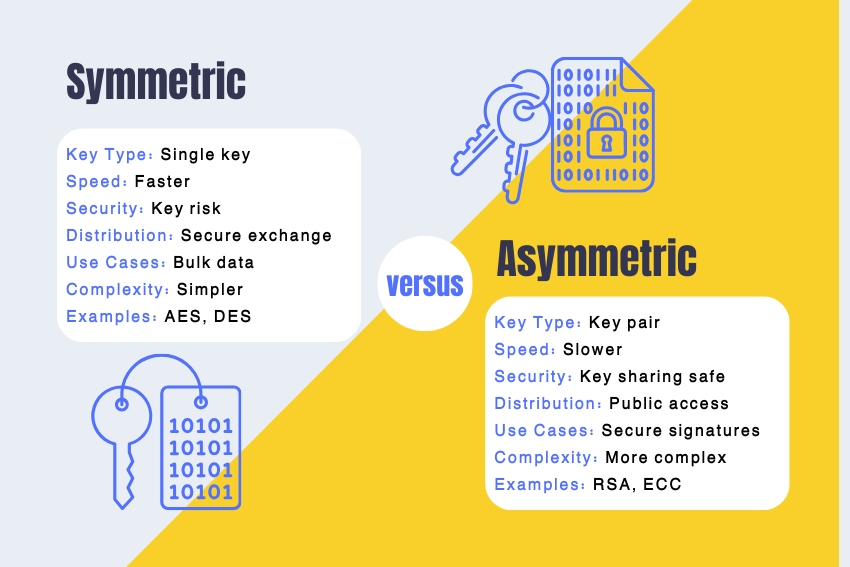
The most apparent difference between symmetric and asymmetric encryption that is visibly noticed by users is that there are two keys involved in this system and practically no similarity between them.
The main differences between symmetric and asymmetric encryption include:
- Type of keys used: The Symmetric Encryption Keynes use a single set of keys while the Asymmetric Encryption Keynes use so called ‘Public-Key’ and ‘Private-Key.’
- Speed/performance: There are algorithms which are rapid and effectual for vaster amount of data enciphering while there are other classifications of ciphers which are slow.
- Scalability: It is for this reasons that symmetric ciphers are not very scalable – each of the communicants must exchange keys individually. With asymmetric encryption it is easier to distribute the keys.
- Security: Diffusion can become an issue given that symmetric principles are used while public keys in asymmetric encryption do not require protection of confidentiality.
- Use cases: We already know that symmetric encryption is more suitable for the encryption of large data sets than asymmetric encryption, which on the hand makes secure multi-party communication easier.
The table below summarizes some of the main differences between Symmetric vs Asymmetric Encryption:
| Property | Symmetric Encryption | Asymmetric Encryption |
|---|---|---|
| Type of the keys | Single shared key | Public and Private key pair |
| Speed | Very fast | Slow |
| Scalability | Vulnerable – the exchange of secure keys is difficult | Robust – Public keys can be shared publicly |
| Security | Keys must be exchanged in such a secure manner | Public keys do not require protection |
| Application Areas | Mass encryption (storage, transfer, databases etc. | Connections (TLS/SSL), signing, key-sharing |
On this basis, symmetric key encryption should be used where there will be repeated data transfers between the sender and the receiver while asymmetric key encryption should be used where there will be key transfer between the two parties.
Symmetric vs Asymmetric Encryption: When to Use Each Type?
Symmetric Encryption
Symmetric encryption is best suited for scenarios where speed and efficiency are critical. Some common use cases include:
- Bulk Data Encryption: When encrypting large volumes of data, such as in database encryption or file storage, symmetric encryption can process the data more quickly.
- Real-Time Communications: Applications like video conferencing and voice-over-IP (VoIP) that require low latency and high performance can benefit from symmetric encryption.
Asymmetric Encryption
Asymmetric encryption is more appropriate for situations where secure key exchange and enhanced security are paramount. Typical use cases include:
- Secure Key Exchange: Protocols like SSL/TLS use asymmetric encryption to exchange symmetric keys securely, ensuring encrypted communication over the internet.
- Digital Signatures: Asymmetric encryption is commonly used in digital signatures to verify the authenticity of messages and documents, ensuring integrity and non-repudiation.
Hybrid Approaches
In practice, many systems employ a combination of both symmetric and asymmetric encryption to leverage the strengths of each method. For example, during a secure online transaction:
- Asymmetric encryption is used to securely exchange a symmetric key.
- The symmetric key is then used to encrypt the bulk of the data exchanged during the session.
This hybrid approach maximizes security while maintaining efficiency.
How Symmetric and Asymmetric are used collectively?
Symmetric and asymmetric encryption are complementary technologies that work together in modern cryptography and secure communications:
- Asymmetric encryption means it is possible to get the two parties to interchange symmetric keys safely. This addresses the major issue with symmetric ciphers regarding distribution of keys.
- The symmetric key is also used to encrypt large amounts of data using a faster symmetric cipher.
- The symmetric key can be renewed and transmitted using the slower asymmetric keys.
- The disparity of key pairs further facilitates services like confidentiality, non-repudiation, authentication etc. over the novel symmetric communications channel.
This combined cryptosystem solution is the benefit of both symmetric and asymmetric techniques for efficient and fast secure communication.
Conclusion
Both Symmetric and Asymmetric keys are crucial for protecting information in the world of computers. Asymmetric encryption is thus used for mass data encryption and live data encryption while symmetric encryption is used for encrypting large data sets within a short time. But as pointed often asymmetric encryption is more secure especially in terms of key exchange and sensitive information bit slows down the process.
Thus, anyone who wants to develop a career in cybersecurity, data management, or Information Technology must understand and respect the differences between Symmetric vs Asymmetric keys. It is evident from the analysis that the decision between using symmetric and asymmetric encryption rests on a number. It can also be inferred that the techniques and approaches to encryption will also change over time due to technological advancement in this area of practice calling for professional competency in change.